Guardian Ops
Stop Network Abuse In Its Tracks
Guardian Ops by Abusix is a powerful network abuse prevention platform that helps organizations detect, respond to, and mitigate security incidents. With Guardian Ops, you can safeguard your systems and data from cyber threats effectively.
Guardian Ops in a nutshell
Everything you need to control your network reputation and resolve abuse notifications, all on a single platform
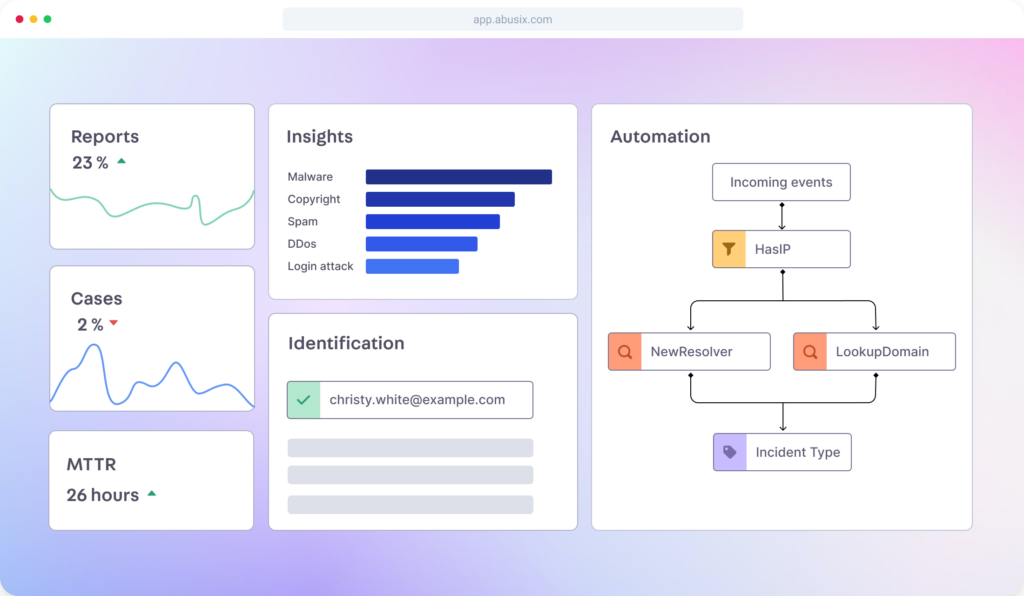
Why Guardian Ops?
Automation
Boost productivity with automated security workflows. Detect threats, alert users, cut costs, and access key reports for smarter decisions.
Network Reputation
Bad network reputation hurts business. With Guardian Ops, be proactive, follow best practices, and ensure customer satisfaction.
Customer Retention
Boost response speed and service. Centralize communication across departments. Simplify takedowns with detailed reports.
Legal Protection
Avoid costly lawsuits with Guardian Ops. Comply with local laws, like handling copyright infringements policies such as a 3 strikes notice.
Automate your busy work
Streamline tasks with Guardian Ops: Automate workflows, boost productivity, enhance network security, cut support costs, and gain insightful reports.
- Detecting and classifying cases
- Parsing and combing events to reports
- Processing reports by customized actions
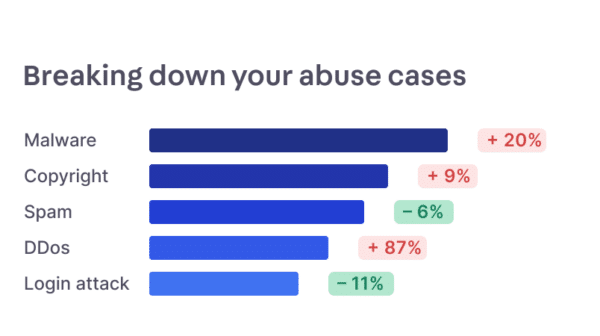
Focus on the most critical cases
Abusix automates manual tasks so you can focus on most critical cases
Enrich reports with metadata
You get enhanced reports with valuable metadata, enriched insights with context, to facilitate more informed decision-making and target responses in abuse management and security practices.
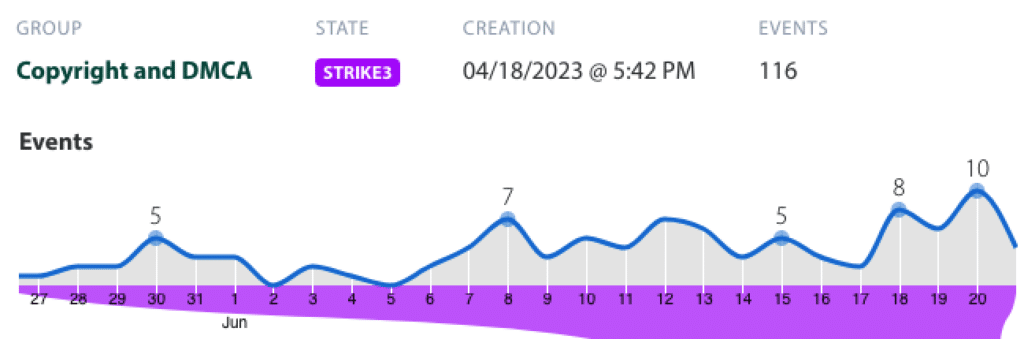
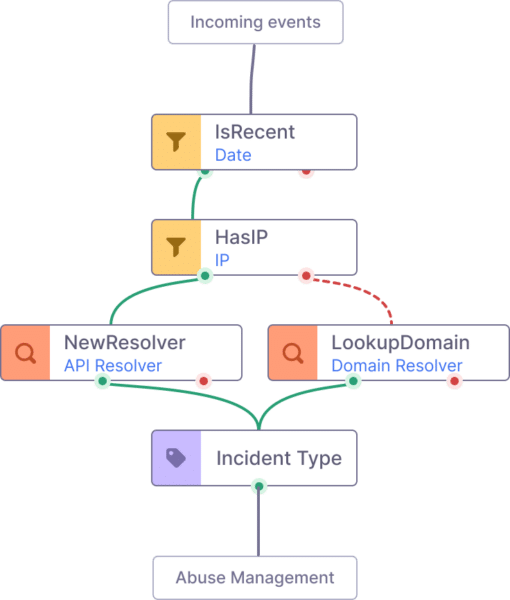
Process reports with tailored playbooks and actions
Customize Abusix platform the way your team works – inbound processing, email templates, parsers, case groups, playbooks… and integrations to your systems
Trusted by Leading Global Brands







What our customers say



Need More Help?
We have a well structured documentation that you can check it out and we are always happy share more knowledge with you. So you know what to do, right? Click it and get those nuggest 😉

Abuse Desk Management Course
Join our 10-day course and become a pro at managing network abuse.

Documentation
Check our well structured documentation and dive in to learn more.
Get in touch
You don't need to be an expert to detect abuse in your network, you just need the right tool.
Start free today, or reach out. We’re happy to help.
