The Power of Real-Time Threat Intelligence
Protecting networks, ISPs, and businesses with global-scale cybersecurity data.
Trusted by Leading Global Brands











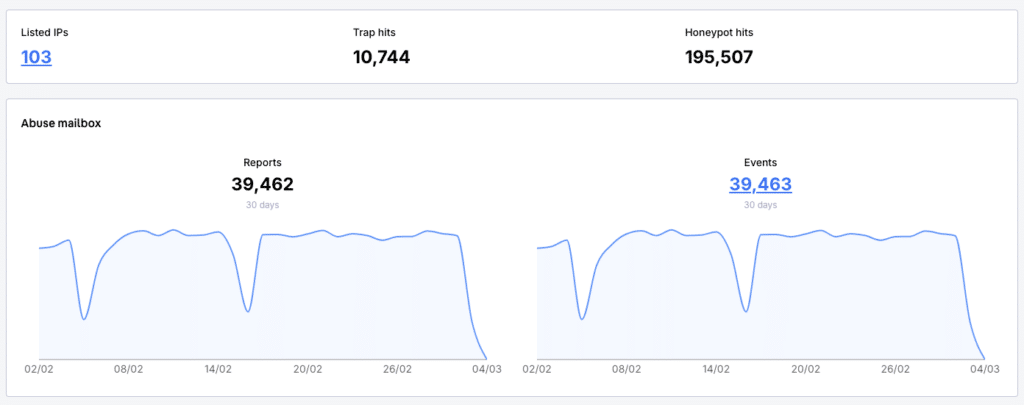
By the Numbers
Elevate Your Network and Email Security
Streamline your security setup with a straightforward, four-step process to enhance cybersecurity and threat prevention.

Insights
Quickly ingest and visualize data to detect abusive behavior across your network, enabling enhanced cybersecurity insights and actionable intelligence.

Automation
Automate security workflows, detect early threats and reduce support costs with comprehensive and detailed network security reports.

Protection
Access in-depth network reports, top issues, and alerts to stay ahead with abuse prevention, cybersecurity innovation & network security.

Integration
Seamlessly integrate with alerts and system logs to ensure comprehensive, real-time network security and enhanced threat detection.
Comprehensive Network and Email Security Solutions
Abusix processes 39K+ security events monthly, analyzing real-time threats to prevent cyberattacks at scale.
Real Experiences, Real Impact


join us FOR a SAFER INTERNET
Your Network. Your Email. Your Clients.
Together, let’s make the internet safer for everyone through top-level Cybersecurity Innovation & Network Security.




